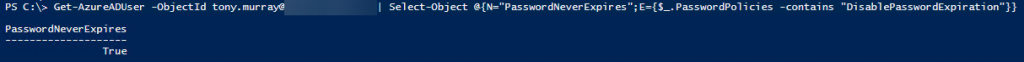
One of my customers is using Password Hash Synchronisation (PHS) as their Azure Active Directory authentication method for users synced from on-premises AD. Not having had much experience with PHS, I was a little surprised to learn recently that PHS users have cloud passwords that do not conform to the default AAD 90 day expiry. Instead, password expiry is disabled for synchronised users when PHS is enabled. How can you check this? Well, with a little Powershell.
Get-AzureADUser -ObjectId tony.murray@contoso.com | Select-Object @{N="PasswordNeverExpires";E={$_.PasswordPolicies -contains "DisablePasswordExpiration"}}
If you want to get a comprehensive report about password expiry for all user Azure AD users, then I can recommend this one from the Technet Gallery: PwdExpiryReport.ps1
I think the reason why the cloud user passwords are set to never expire with PHS enabled is that it removes the potential negative impact of mismatched password policies between on-premises AD and Azure AD. For example, it would very confusing for a user if their AAD password expired while their on-premises AD password was still valid.
